The Fraud Explorer
Software antifraude que pronostica, previene y detecta la corrupción, el fraude y el abuso organizacional en las comunicaciones corporativas
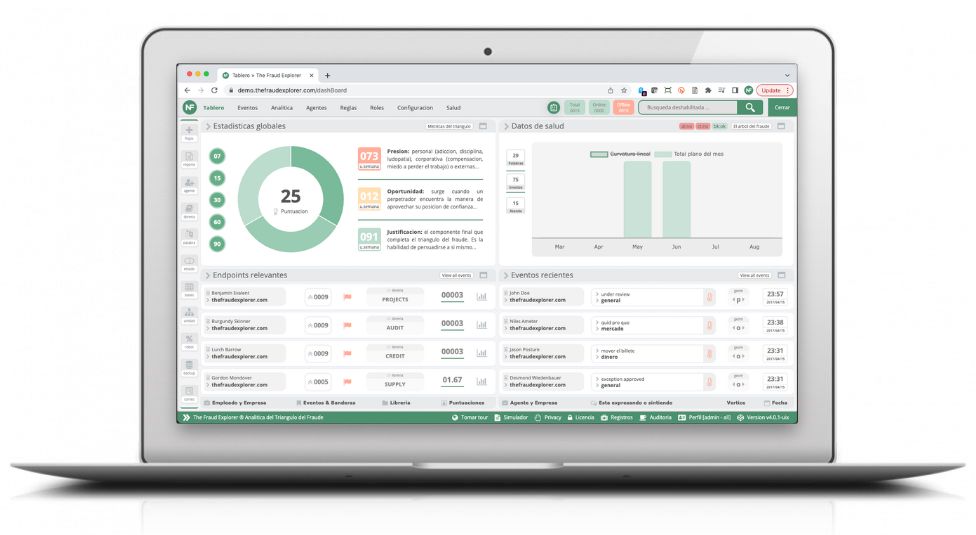
Estadísticas de términos, métricas e informes
Agentes que más reportan eventos
Estadísticas de palabras procesadas
Últimos eventos del triángulo del fraude







